RANDOM PAGE
SITE SEARCH
LOG
IN
SIGN UP
HELP
To gain access to revision questions, please sign up and log in.
A2
aKey Exam Facts
bCircuit Switched Networks (Telephone)
The original telephone network was circuit switched.

- Human operators connected the circuits.
- More recently electro-mechanical switching was used.
- The most recent upgrade introduced digital switching.
This style of network has one advantage but several problems.
- The advantage: You get exclusive use of the connection. You get 100% of the available bandwidth.
On packet switched networks you have to share the cables with other users.
- You can run out of circuits leading to messages like "All the lines to Manchester are busy. Please try later."
- For much of the time, there were many unused circuits. These still cost money.
- Phone calls were expensive.
- You paid for the time spent making calls.
- Connecting the calls took several seconds.
cPacket Switched Networks (PSN)
Warriors of the Net - Cheesy PSN Video 13 Minutes

This Internet-Map image is part of a larger one on Wikimedia Commons showing an extended star / mesh network.
- The first packet switched networks were used for computer data.
- Many computers shared the same cables.
- Everyone was permanently connected to the network.
- There were no dial-up connection delays.
- You paid for the bits or more likely megabits of data exchanged.
- Home users pay a flat rate but have maximum usage limits.
- Data was transmitted in short bursts called packets, allowing many machines to share the same cables.
- Smaller networks are interconnected via devices called routers.
- TO CONNECT A COMPUTER TO THE INTERNET ...
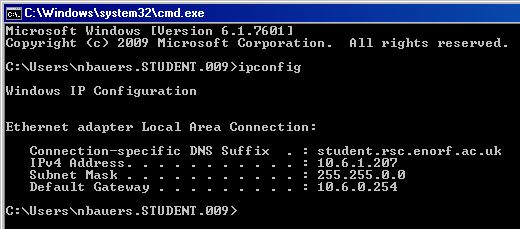
- The computer must have an IP ADDREESS
- The computer must have a SUBNET MASK
- The computer must have a DEFAULT GATEWAY
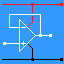
- The Default Gateway or Edge Router sits at the boundary between your local network and the rest of the world.
dTCP/IP and IP Addresses
- Data packets use Internet Protocol (IP) addresses identifying the destination and source computers.
- A protocol is an agreed set of electronic rules to allow communication.
- Using many small packets allows many machines to share the same cables. This is a kind of time division multiplexing.
- Shared cables lead to poorer security but encryption solves that problem.
- TCP is the transmission control protocol. This deals with acknowledging received packets and organising the re-transmission of lost or damaged packets.
- Because of the cable sharing, the costs were much lower per user compared with circuit switched networks.
- Data could be re-routed, avoiding congested or failed routes, making this type of network more reliable than the telephone circuit switched style. So you say goodbye to the "All the lines are busy" messages.
- The performance of PSNs soon improved making it possible to send voice or music. VoIP (voice over IP) was invented.
- Organisations like Skype invented the idea of the Internet phone call. These calls were free (ignoring the fees to connect to your service provider.)
- Major telecommunications companies began to replace their circuit switched networks with packet switched, taking advantage of the lower costs and better performance.
- The performance is now so good that most data is sent over packet switched networks, including phone calls which use virtual circuits simulating the original circuit switched networks. Even TV and Radio use the PSNs because of the cost advantages.
- QoS, quality of service technology now exists to guarantee minimum amounts of bandwidth to organisations with guaranteed service level contracts.
- IP phones can now plug into most computer networks so separate wiring is not needed for internal phone systems.
- Mobile phone networks also use packets to transfer voice and data.
eUDP for Audio and Video Streaming
- High definition TV and Video-on-Demand is now distributed to subscribers over fibre-optic cables using packet switching technologies.
- UDP packets are sent with no system of acknowledgements. This is more efficient but lost packets are not re-sent. This is OK for audio or video because a few lost packets reduce the quality but the stream still works.
- UDP = User Datagram Protocol
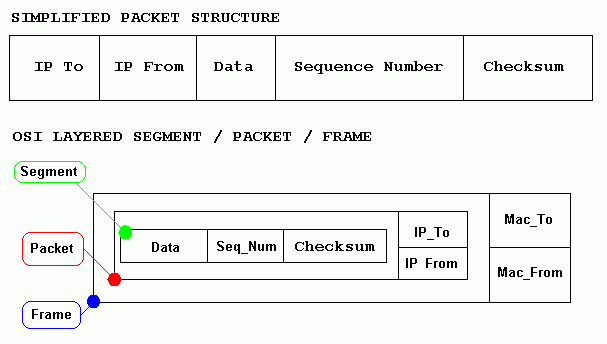
fEncapsulation, Segments, Packets, Frames and Bits
There is a great deal of confusion about packet terminology. Many packets should not be called packets! TCP segments are wrapped or encapsulated inside IP packets. The IP packets are encapsulated inside Ethernet frames.
To grasp the idea of encapsulation, think of a letter inside an envelope inside a mail sack inside an aircraft. The envelope, the sack and the aircraft all carry addressing information (the pilot knows where to fly to but is not interested in the address labels on the letters). The sack will be labelled with a sorting office address. The letter carries the street address.
Internet addressing is quite similar. There is a MAC address which identifies a local hardware device. There is the IP address which has two portions. The network number identifies the destination network and the host address identifies a machine on the destination network.
Routers are mainly interested in IP address network numbers which are used to forward packets onto the next hop of their journey.
Switches are mainly interested in MAC addresses. The switch learns these so they can send data to the correct local hardware device.
gSegments
Assume you want to send quite a large chunk of data across the network ...
- The data is usually too big to be sent in one chunk so it is sliced up into smaller pieces called SEGMENTS.
- The segments are numbered. If they arrive in the wrong order, they can be sorted to re-create the original data.
- TCP uses the segment numbers to acknowledge the arrival of the data and to request the retransmission of lost segments.
- TCP also re-assembles received segments into the correct sequence-number order.
- Segments do not contain any addressing information.
hPackets
- IP packets travel one or more hops, through multiple routers.
- The data segments above are wrapped or encapsulated inside IP packets.
- The IP packets have a destination IP Address
- The IP packets have a source IP Address
- There is a header checksum. This is used to detect damage to the packet. Damaged packets are discarded.
- The packet has a protocol field containing for example ...
- http (web page data - hypertext transfer protocol)
- ftp (a file transfer - file transfer protocol)
- smtp (an email message - simple mail transfer protocol)
- There are lots more.
iFrames
- The packets above are are encapsulated inside frames.
- The frames have a destination MAC address used to identify the destination device.
- The frames have a source MAC address used to identify the originating device.
- Frames travel one hop, from one hardware device to another.
- The most widely used frame based protocol is Ethernet.
- Ethernet "packets" are frequently mentioned in the literature. Strictly speaking, this is wrong; they should be called frames.
jBits
- The hardware devices take the frames and transmit or receive them serially, one bit at a time.
- The transmission is either
- D.C. pulses (baseband) sent along Ethernet cables.
- Light Flashes sent over optical fibres also encoded using Ethernet rules.
- Radio Frequency pulses sent between WiFi hotspots and end-devices.
- Multiple modulated radio frequency carriers (broadband).
kLANs and WANs
lLocal Area Networks
LANs are confined to a single site such as a home, school or small business.
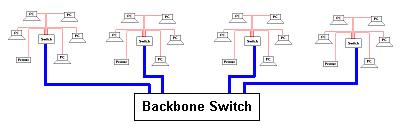
This diagram shows the smallest home or business network with a handful of computers.
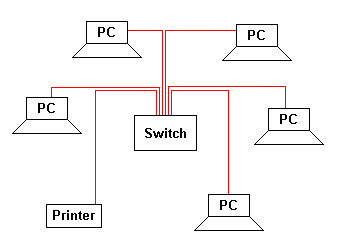
- CAT5e copper unshielded twisted pair cable is most commonly used inside buildings. There is a 100 metre length limit.
- WiFi wireless networks often replace the copper cables.
- Fibre optic links are used between buildings and these can go much further.
Bigger networks have backbone switches linking the smaller network segments with fibre-optic cables.
mWide Area Networks
WANs are made by interconnecting LANs using ROUTERS.
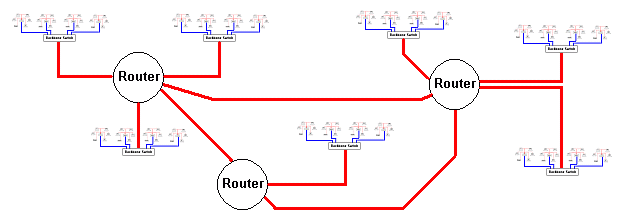
- This image shows LANs linked by multiple routes via ROUTERS.
- The big advantage is that routers learn the best routes and can automatically re-route traffic to avoid congestion or failed routes.
- WANs are connected using serial links.
- Phone lines are used as well as co-axial cable.
- Fibre optic links are widely used.
- Microwave links are common.
- You can easily spot the microwave dish antennas beaming horizontally between hill-top masts. Tall buildings are used too.
- Satellite links are used when there is no line of sight path, commonly across oceans.
- Satellite dish antennas point up into the sky.
Here is a WAN map showing thousands of routes, all interconnected via routers.

nEthernet
This is a very widely used protocol (a set of rules) for many hosts (computing devices) to share a network. With the original Ethernet all the hosts shared the same cable so rules were needed to make this possible.
- If the cable is in use, no one else can use it. Wait for the cable to be "silent".
- If the cable is silent, anyone can use it to send a "frame". No one has priority.
- If by chance two or more hosts attempt to send a "frame" at the same time, a collision occurs.
- After a collision, all hosts wait for a random (and usually different) length of time before re-trying the transmission from step 1.
oLittle or Big Packets
Networks and especially long distance networks are unreliable. Sending one big packet would never work.
Little Packets - GOOD
- If 100 packets are sent, maybe only 90 arrive undamaged.
- 10 need to be re-transmitted and of these, perhaps 9 arrive intact.
- This leaves one damaged packet to re-transmit.
- There is a 90% chance it will arrive safely on this third attempt.
One Big Packet - BAD
- If one big packet had been sent it would arrive damaged in 10 unknown places.
- If you send it again, it arrives damaged 10 times in different places.
- However many times you try, it always arrives damaged.
Using small packets, the transmission was 100% successful after sending 111 packets. With one big packet, the transmission would never succeed. These numbers are just an example. Real networks are more random.
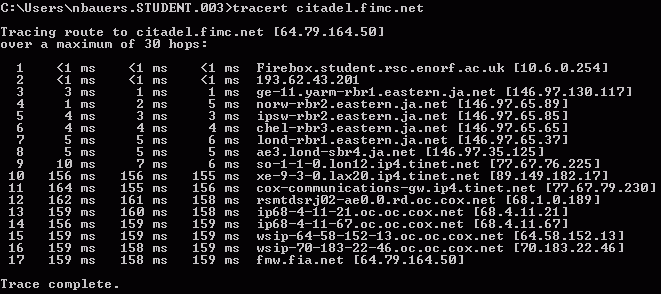
ptracert
The Windows tracert command lists every router between your computer and the destination you specify. It is a useful diagnostic tool if the Internet seems to be broken.
To try this exercise, open a command shell window. Hit Windows-Key+R and type CMD. In this window, copy the command in the screen shot or try it with any other web address you are interested in.
This image shows traffic from the UK to the USA being routed via Yarmouth, Norwich, Ipswich, Chemlsford and London. It takes 6ms to bounce a signal back from London. Tinet handles the transatlantic link and the hop times are now 150 ms or more. In the USA, Cox Communications routers are handling the traffic. The final destination is Pacifica Radio in Los Angeles although their web server could be located elsewhere.
Most operating systems have something equivalent to tracert - Google will know.
reviseOmatic V3
Contacts, ©, Cookies, Data Protection and Disclaimers
Hosted at linode.com, London







